Pyramid of Pain - Threat Hunting
- GK
- Nov 4, 2024
- 5 min read
The Pyramid of Pain is a concept developed by security expert David Bianco. It’s a framework designed to help cybersecurity teams understand the types of indicators of compromise (IOCs) they encounter during threat hunting or incident response, and how challenging it is for adversaries to evade detection based on each type of indicator. By using the Pyramid of Pain effectively, cybersecurity teams can prioritize their efforts to disrupt attackers’ activities more effectively.

I studied this as part of a "TryHackMe" exercise, which is accessable from here: https://tryhackme.com/r/room/pyramidofpainax
What is the Pyramid of Pain?
The Pyramid of Pain is a model that categorizes different types of IOCs and illustrates the levels of difficulty an attacker faces in evading detection. It is called a "pyramid" because the structure is hierarchical, with the least painful (easiest to change) indicators at the bottom and the most painful (hardest to change) at the top.
The goal is to move up the pyramid, where actions taken by the defensive team (blue team) make it more difficult for attackers (red team) to maintain access or avoid detection.
Layers of the Pyramid of Pain
Each level of the pyramid represents a type of IOC and the relative "pain" it causes attackers when detected:
Hashes (Bottom Level)
Description: Cryptographic hashes (e.g., MD5, SHA1) are used to uniquely identify specific files.
Challenge for the Attacker: Low.
Why It Matters: Attackers can easily modify file hashes (e.g., by making small changes to files) to avoid detection, so relying solely on hashes is not effective.
Detection Tools:
VirusTotal and Cuckoo Sandbox: Both tools allow file analysis and hash lookup against known malware databases.
YARA: Rules can be configured to match specific byte patterns in files, supplementing hash-based detection.
SIEMs (e.g., Splunk, IBM QRadar): Hash values can be ingested and compared against threat intelligence feeds in real-time.

IP Addresses
Description: IP addresses used by attackers’ infrastructure.
Challenge for the Attacker: Low to moderate.
Why It Matters: Attackers can quickly change IP addresses or use multiple ones, so detection through IP addresses is only somewhat effective.
Detection Tools:
Threat Intelligence Platforms (TIPs) such as Recorded Future and Anomali: These platforms provide updated IP reputation data that integrates with SIEMs.
Firewalls and Intrusion Detection Systems (e.g., Snort, Suricata): Rules can be set to detect and block known malicious IPs.
Threat Hunting Solutions (e.g., Cisco Umbrella): For identifying connections to known malicious IPs in DNS and network logs.
Domain Names
Description: Domain names used by attackers to communicate with malware or phishing websites.
Challenge for the Attacker: Moderate.
Why It Matters: Although attackers can register new domains, it takes time and resources, so identifying and blocking malicious domains is somewhat effective.
Detection Tools:
Passive DNS Solutions (e.g., Farsight DNSDB): Used to analyze historical DNS records associated with suspicious domains.
Domain Generation Algorithm (DGA) Detection: Tools like OpenDNS and Palo Alto’s WildFire detect and block DGA-based domains.
URL and Domain Analysis (e.g., DomainTools, VirusTotal): Domain reputation scoring and registration details analysis are used to identify potentially malicious domains.
SIEM Correlation Rules: Correlation rules in SIEMs can flag repeated connections to flagged domains or anomalous domain access patterns.

Network/Host Artifacts
Description: Artifacts such as registry keys, file paths, or URL patterns that attackers leave on systems.
Challenge for the Attacker: Moderate to high.
Why It Matters: Attackers can change artifacts, but it requires more effort and time. Detection at this level disrupts established tactics and techniques.
Detection Tools:
EDR Platforms (e.g., CrowdStrike Falcon, Carbon Black, SentinelOne): Capable of monitoring host behavior and detecting abnormal file and registry modifications.
Sysmon (System Monitor): Allows deep monitoring of Windows systems for specific artifacts, which can be forwarded to SIEMs like Splunk for analysis.
YARA: Often used to create rules targeting specific malicious file patterns, registry entries, or other known indicators.
MITRE ATT&CK Navigator: Helps map host artifacts to known attack techniques, aiding in proactive threat hunting.

Tools
Description: Software or scripts used by attackers to perform actions (e.g., Cobalt Strike, Mimikatz).
Challenge for the Attacker: High.
Why It Matters: Many attackers depend on a set of standard tools, so detection and blocking of specific tools disrupts their workflow significantly.
Detection Tools:
Endpoint Detection and Response (EDR): Tools like Microsoft Defender for Endpoint, CrowdStrike, and Carbon Black detect the execution of known attack tools and suspicious binaries.
Application Whitelisting: Solutions like AppLocker or Cisco AMP can be configured to block unauthorized tools.
Network Analysis Tools (e.g., Zeek, Suricata): Can be used to detect network traffic signatures associated with common tools.
Deception Technology (e.g., Illusive Networks, TrapX): Deception tools place decoy systems to detect attackers attempting to use their toolkits in network scans and lateral movement.

TTPs (Tactics, Techniques, and Procedures) - Top Level
Description: The methods and processes that attackers use in their operations (e.g., phishing, lateral movement, privilege escalation).
Challenge for the Attacker: Very high.
Why It Matters: TTPs represent fundamental behaviors that are harder for attackers to modify. Detection at this level forces attackers to rethink their strategy entirely.
Detection Tools:
MITRE ATT&CK Framework: A foundational tool for mapping TTPs, it allows analysts to visualize attack paths and develop countermeasures for specific techniques.
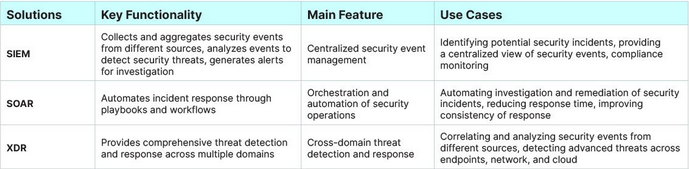
Security Orchestration, Automation, and Response (SOAR): Tools like Splunk Phantom and Cortex XSOAR automate responses to TTPs by analyzing and correlating behaviors across endpoints and network data.
User and Entity Behavior Analytics (UEBA): Platforms like Exabeam and Securonix detect deviations in normal user behavior that could indicate TTP-based attacks.
Threat Hunting and Behavioral Analysis: Using EDR and SIEMs, teams can establish baseline behaviors to detect anomalous tactics in real-time.
Applying the Pyramid of Pain in Threat Hunting and Defense
Step 1: Understand Each Level of the Pyramid
Learn what each indicator type means, where you can find these indicators, and how adversaries typically try to evade them.
Recognize that the pyramid encourages moving away from reactive indicators like hashes and IP addresses towards more strategic ones like TTPs.
Step 2: Develop Detection Rules Based on Pyramid Levels
Build detection and blocking mechanisms at each level:
Use hash-based detections for known malware.
Leverage threat intelligence feeds to detect and block suspicious IP addresses and domains.
Set up rules to detect network and host artifacts based on known malware behaviors.
Track known attacker tools and set alerts on their activity.
Develop detection capabilities around common TTPs, especially those used by specific threat actors.
Step 3: Prioritize Actions That Cause Maximum “Pain” to Attackers
Focus on indicators higher in the pyramid, as they are harder for attackers to change:
For example, identifying TTPs and artifacts can have a long-lasting impact on an attacker's ability to operate.
Use MITRE ATT&CK framework to map and track TTPs effectively.
Step 4: Continuous Monitoring and Adjustment
Continuously update IOCs and detection rules, as attackers frequently evolve.
Regularly review and adapt defense strategies based on the latest threat intelligence and attacker TTPs.
Ensure that blue teams are familiar with common adversary TTPs, so they can detect deviations in behavior.
Step 5: Utilize Threat Intelligence Effectively
Enrich detection and hunting with threat intelligence feeds that provide fresh IPs, domains, and artifacts associated with threat actors.
Focus more on intelligence around tools and TTPs, which provide insights into attacker behaviors and methods that are harder to alter.
Conclusion
The Pyramid of Pain is a valuable tool for prioritizing efforts in cybersecurity. By focusing on indicators higher up the pyramid, cybersecurity teams can maximize the difficulty attackers face, leading to more robust and proactive defenses. Rather than chasing easily changeable indicators, the emphasis shifts to disrupting fundamental tactics and techniques, thereby creating a more resilient security posture.

Comments